20 Domain Name Hijacking Example In This Year

Reverse domain name hijacking also known as reverse cybersquatting or commonly abbreviated as rdnh occurs where a rightful trademark owner attempts to secure a domain name by making cybersquatting claims against a domain name s cybersquatter owner.
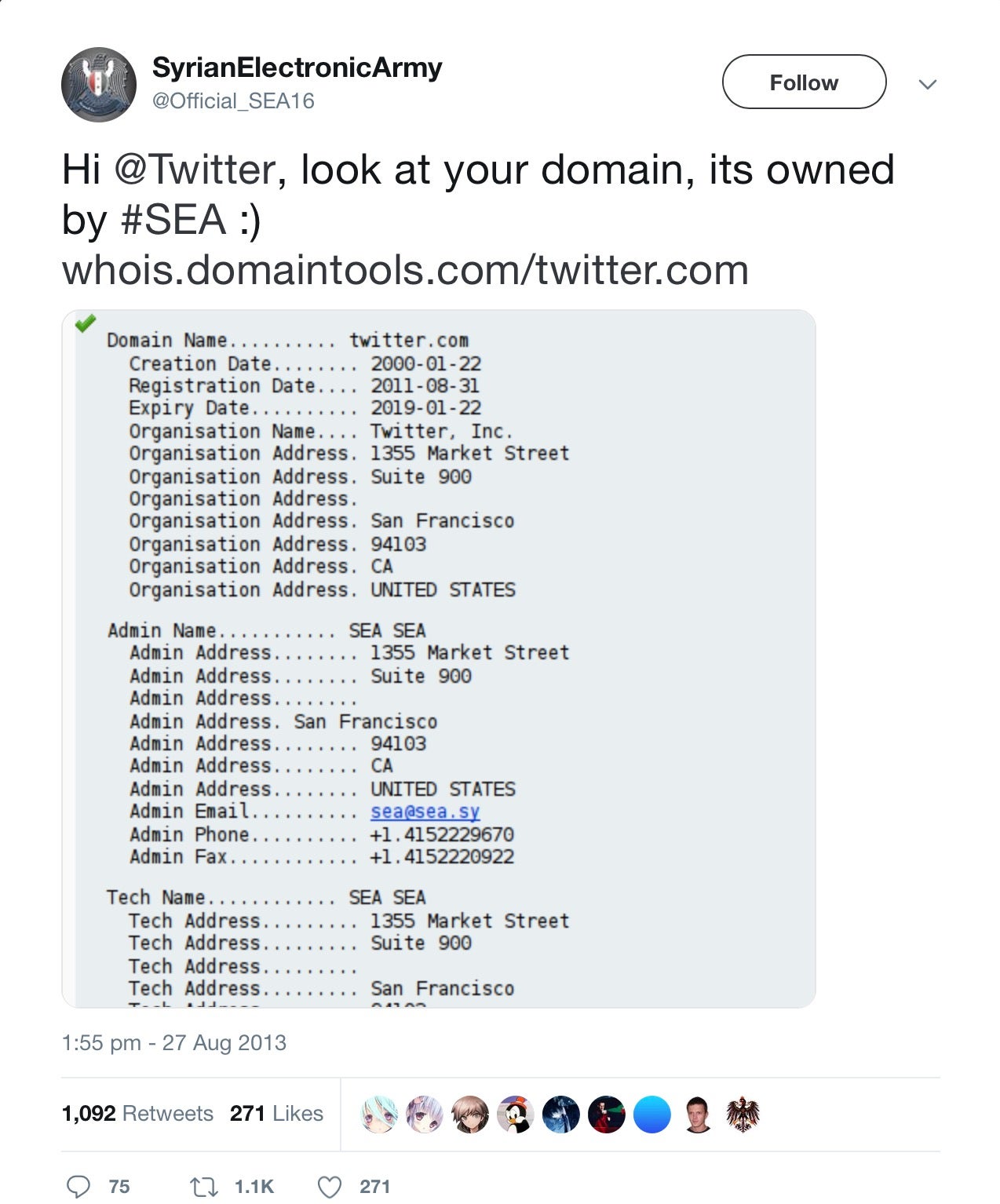
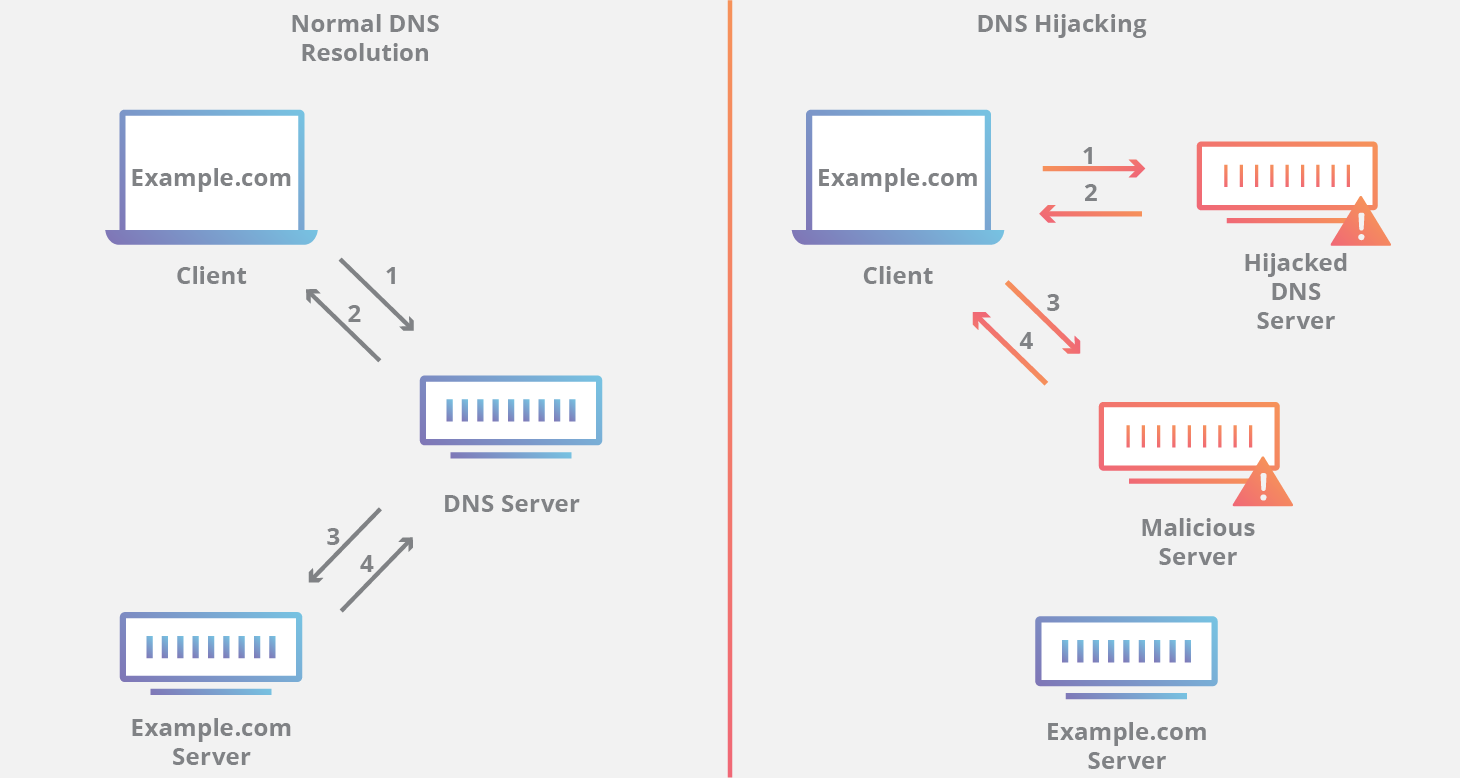
Domain name hijacking example. Domain hijacking is broadly defined as an attempt to transfer ownership or control of a domain from its rightful owner. This sort of activity often harms the legitimate domain owner. Cache poisoning is another way to achieve dns spoofing without relying on dns hijacking physically taking over the dns settings.
Have not adopted basic security measures to guard their portfolio of domain names. The two incidents illustrate the growing threat of domain name system dns hijacking. So to hijack a domain you need not gain access to the target web server.
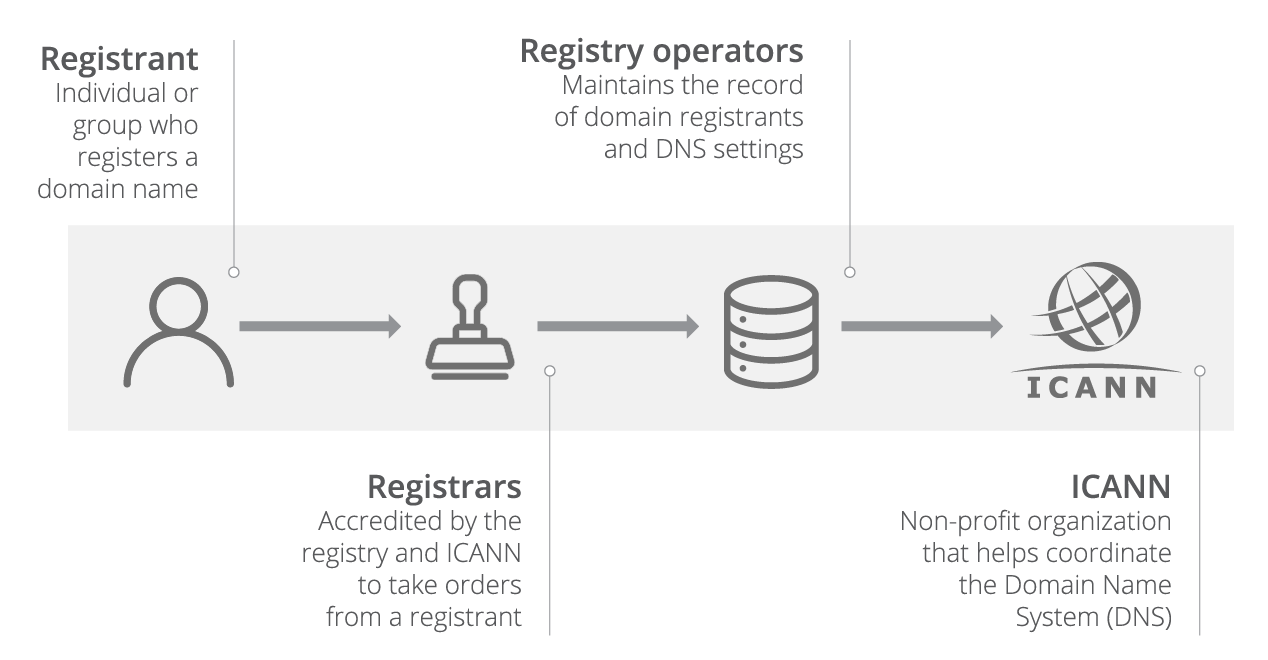
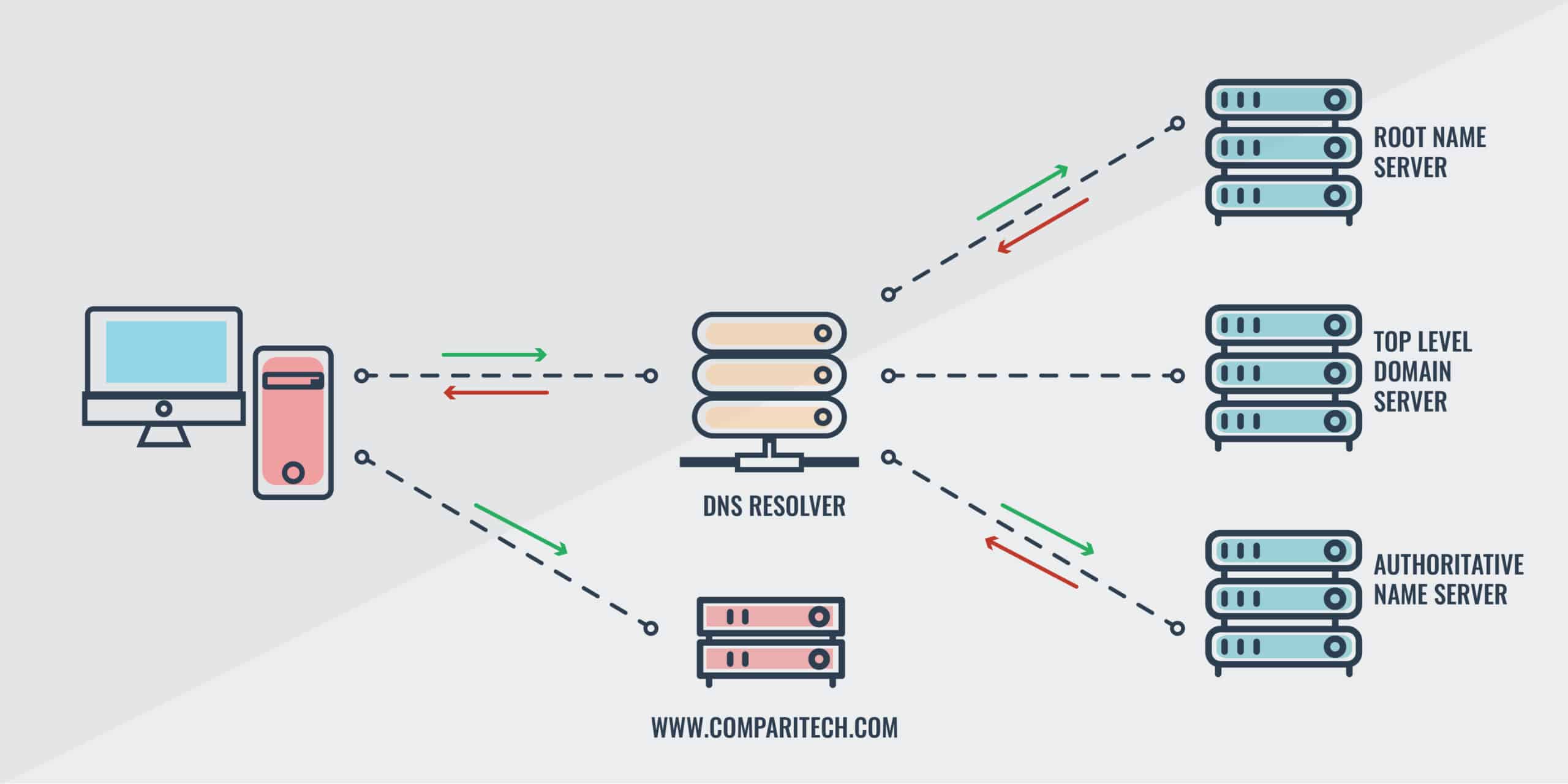
Dns servers routers and computers cache dns records. Domain hijacking often involves a fraudulent registrar transfer request or otherwise false change the registration of a domain. In fact the rate at which domain hijacking has grown has outpaced the growth of domain names.
Basketball superstar mark madsen unknowingly bought a stolen or hijacked url by way of ebay auctions rather than the more common auction sites such as snapnames. For example the. In 2005 says mohan fewer than 100 million domain names populated the internet.
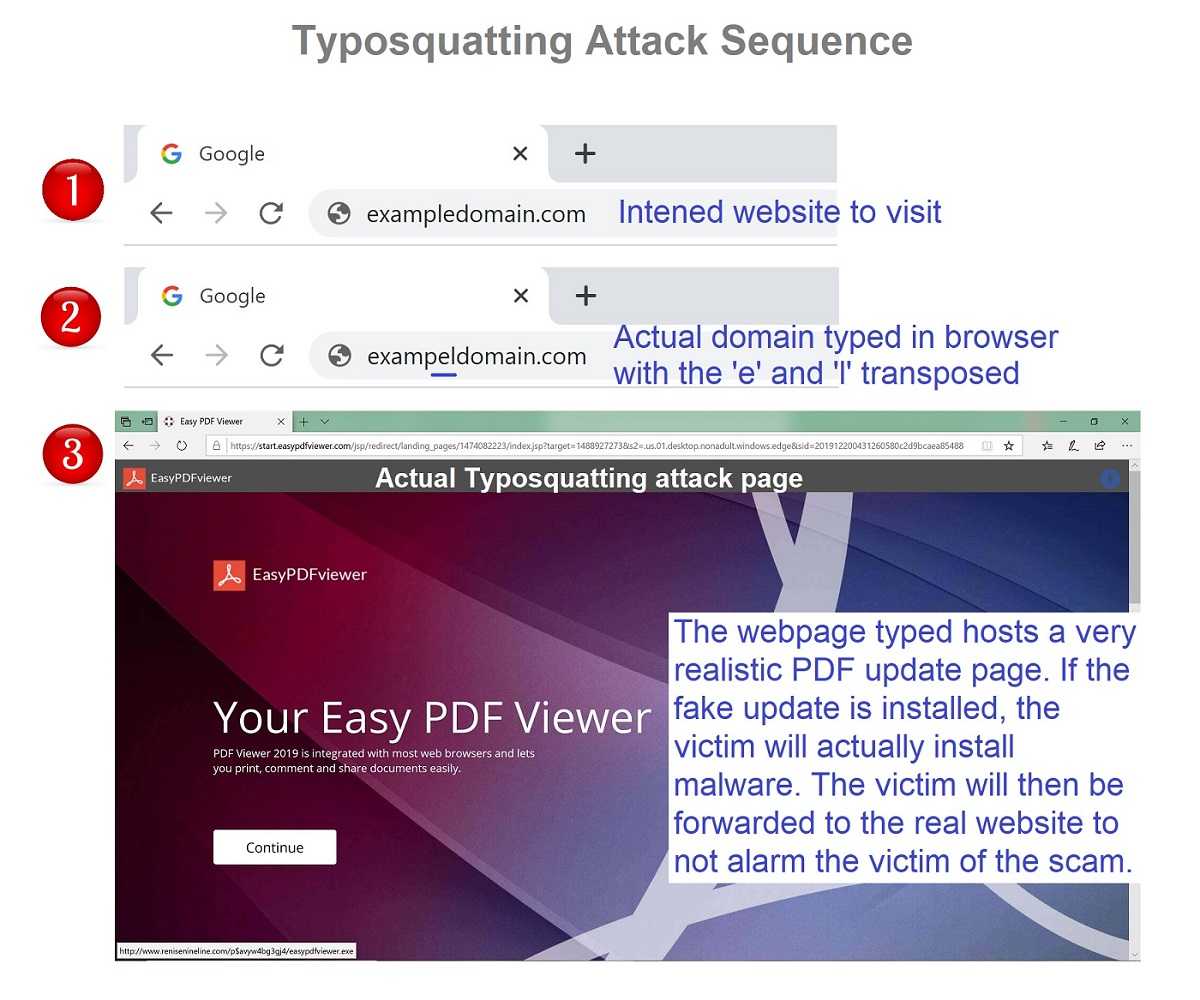
This often intimidates domain name owners into transferring ownership of their domain names to trademark owners to avoid legal action. Phishing and scam emails are usually sent by forging a trusted sender s email address or domain name. For example attackers can compromise a dns server and in this way spoof legitimate websites and redirect users to malicious ones.